GUIDING QUESTIONS
What are political,
social, and economic consequences of internet shutdowns?
How do ISPs typically manipulate access to internet services?
In what
way can internet shutdowns be seen as illegal or illegitimate?
LEARNING OBJECTIVES
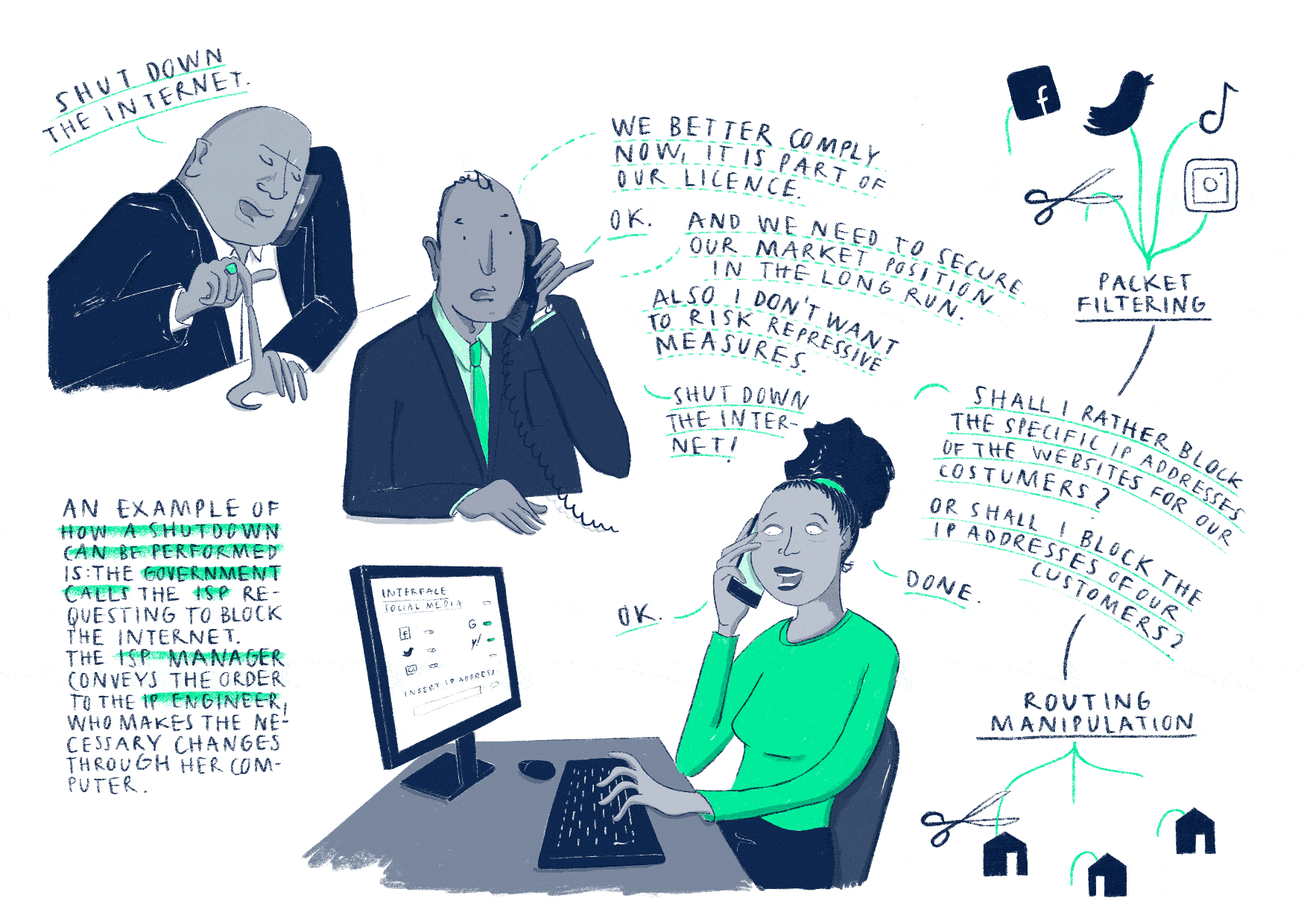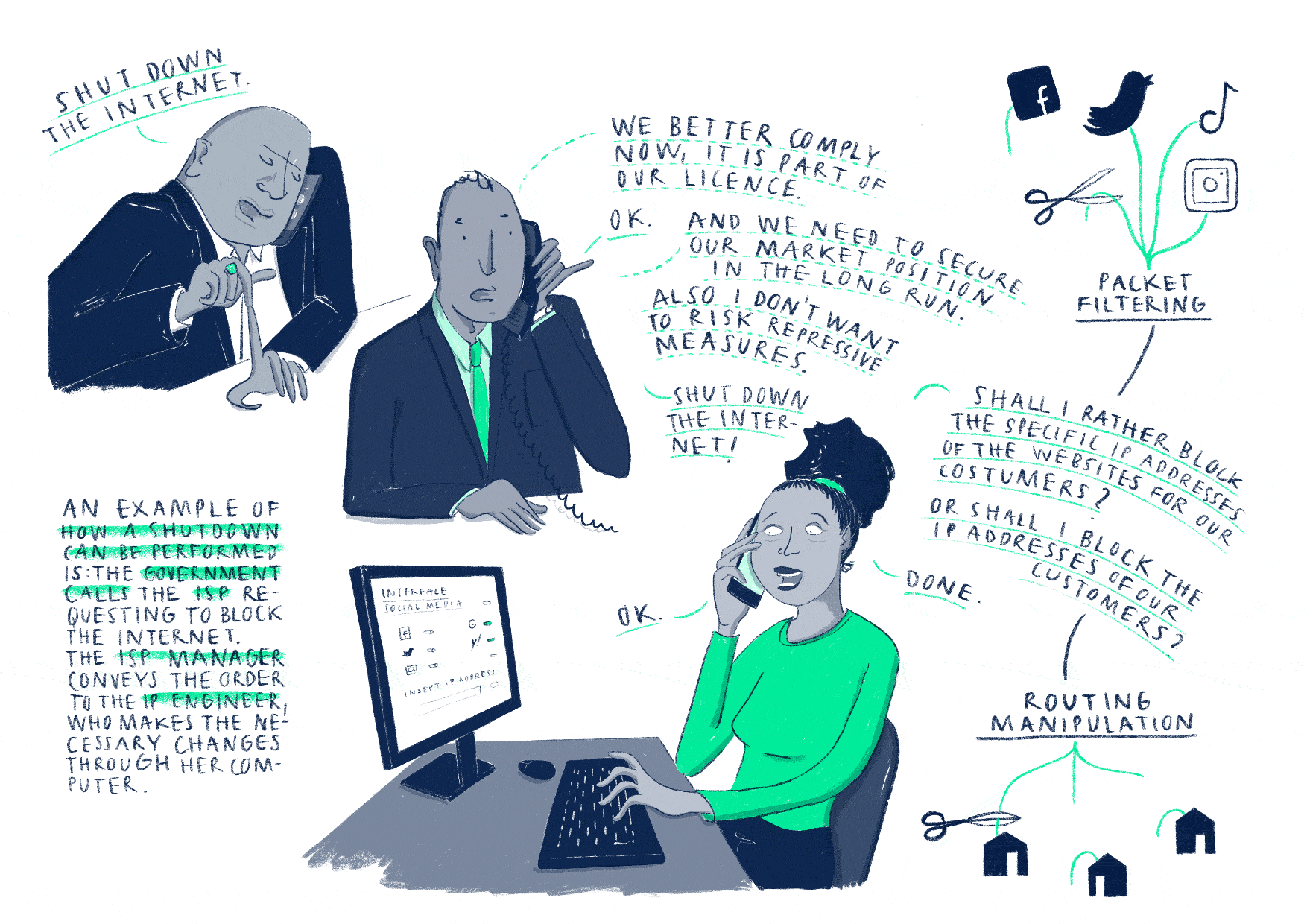
This story
discusses government-requested internet disruptions, their implementation and
consequences.
Internet
disruptions have become a popular tool to control the digital flow of
information and communication, especially in autocracies during politically
contentious times.
The most common
technical strategies rely on internet service providers (ISPs) to manipulate
their routing (1) or packet forwarding (2) mechanisms. ISPs can vary in
their reaction to censorship requests since each ISP runs its own physical
network.
(1) If an ISP withdraws
its Border Gateway Protocol (BGP) routes from the internet, the
blocks of IP addresses that have been allocated to it by the regional internet
registry disappear from the internet. Its customers cannot access websites,
send and receive email, use voice services, or anti-censorship tools such as
VPNs.
(2) Using
information about source and destination of a packet, notably the IP address,
an ISP can manipulate access control lists so to deny traffic to or from
a specific IP address, such as 104.244.42.193 for www.twitter.com. Its
customers cannot access this particular service, unless they access the
internet with an alternative IP address through a VPN.
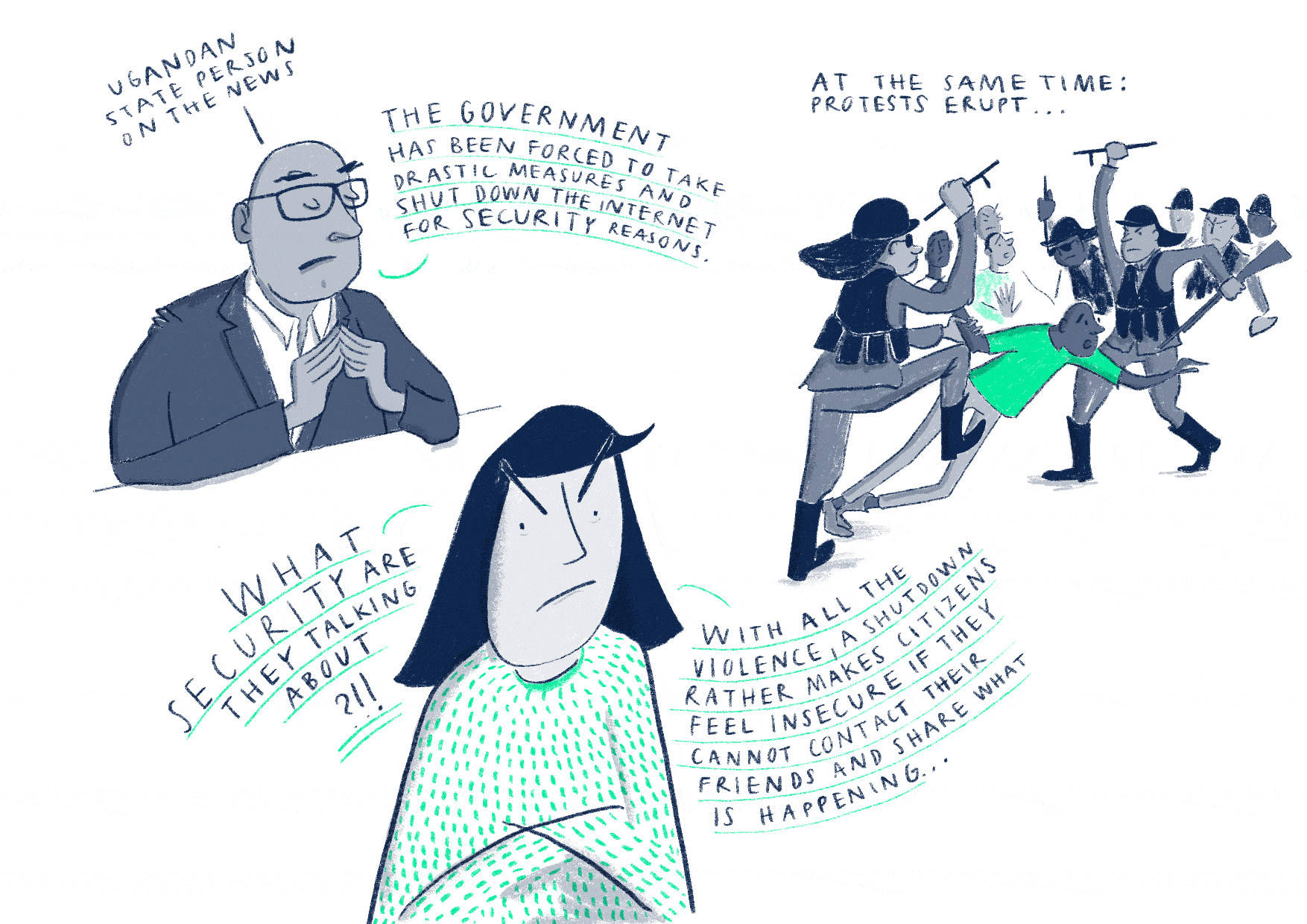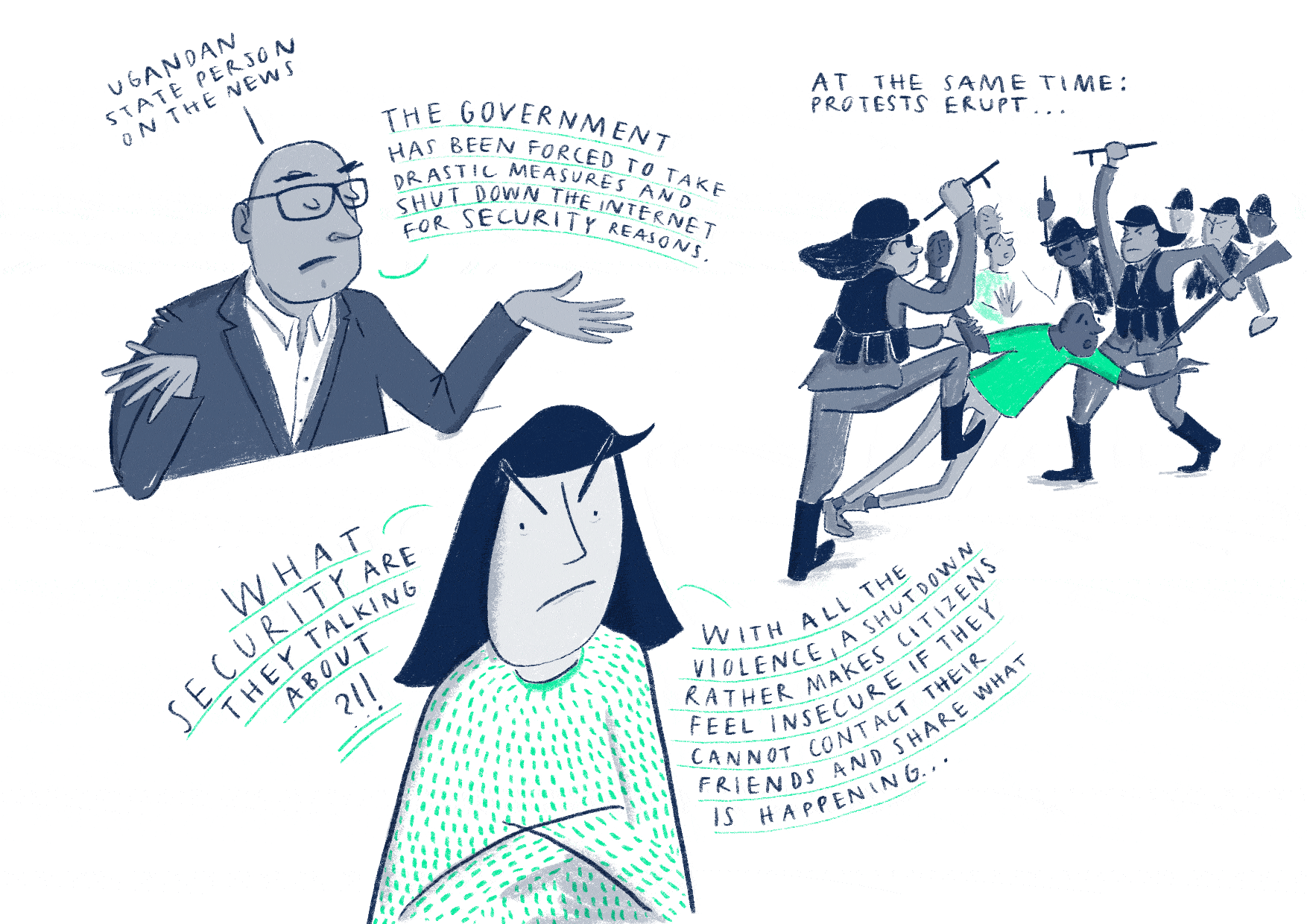
Internet
disruptions have far-reaching economic, social, and political consequences. They limit business-customer communication and prevent citizens from
holding institutions accountable, among others. The United Nations considers
internet disruptions, regardless of the justification provided, to be
disproportionate and a violation of Article 19 of the International
Covenant on Civil and Political Rights. They call upon all states to ensure
that internet access is maintained at all times, including during times of
political unrest.
REFERENCES
DE GREGORIO, G., & STREMLAU, N. (2020). Internet Shutdowns and the Limits
of Law. International Journal of Communication 14: 4224-4243.
Discussion of the limits of law with regard to the imposition and
implementation of shutdowns. In exploring the justifications of shutdowns, the
authors advocate for more transparency around decision-making processes behind
shutdowns.
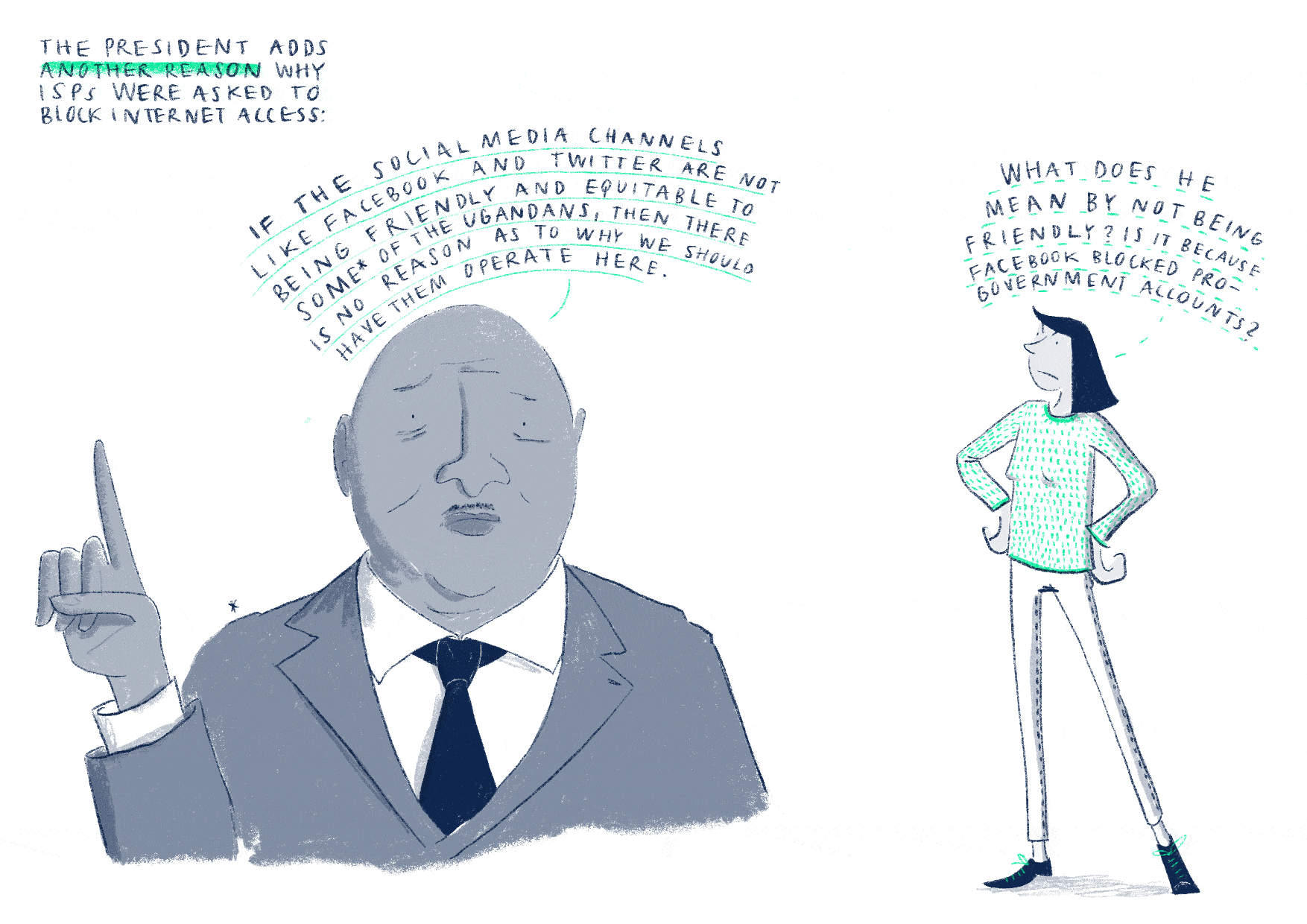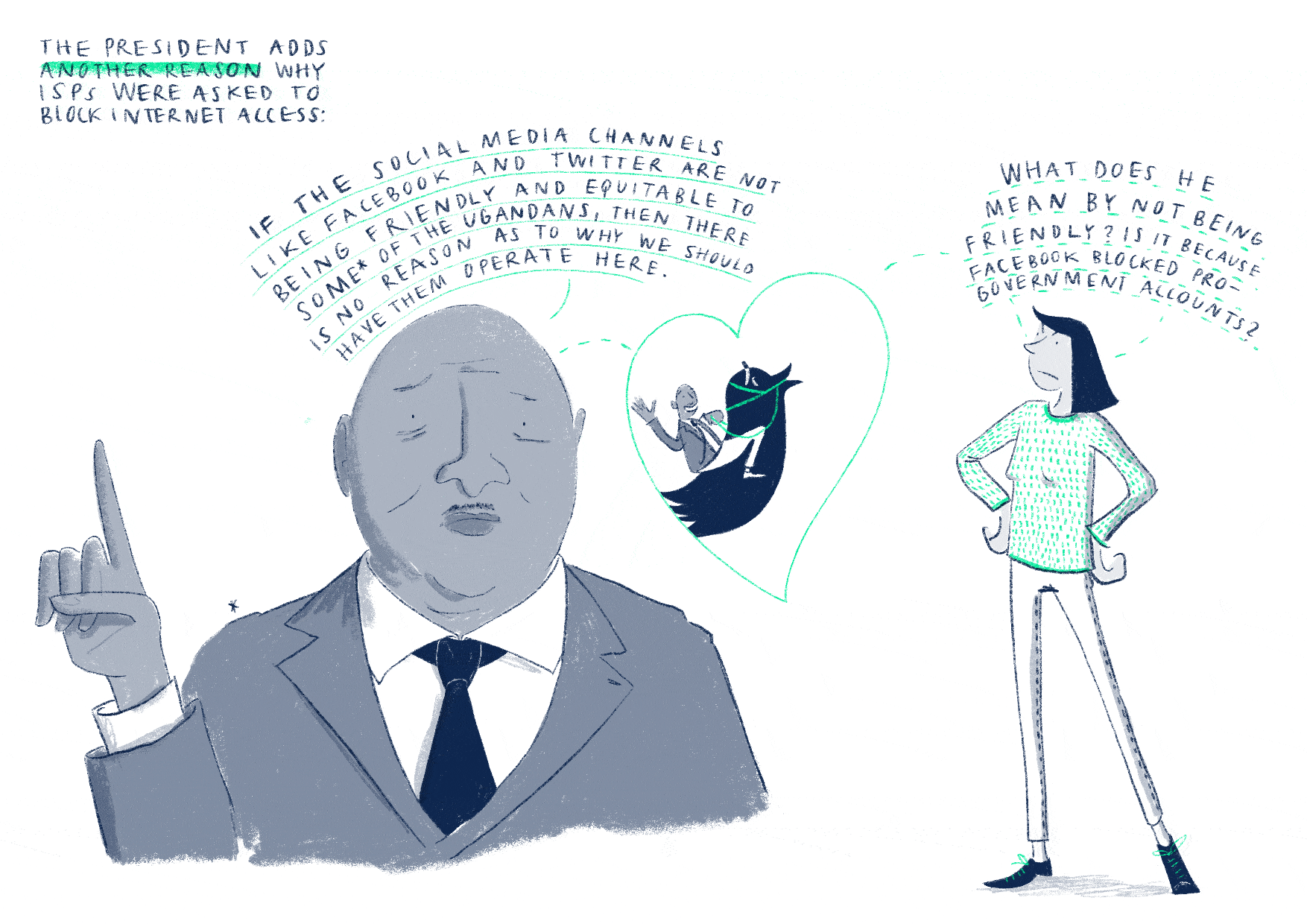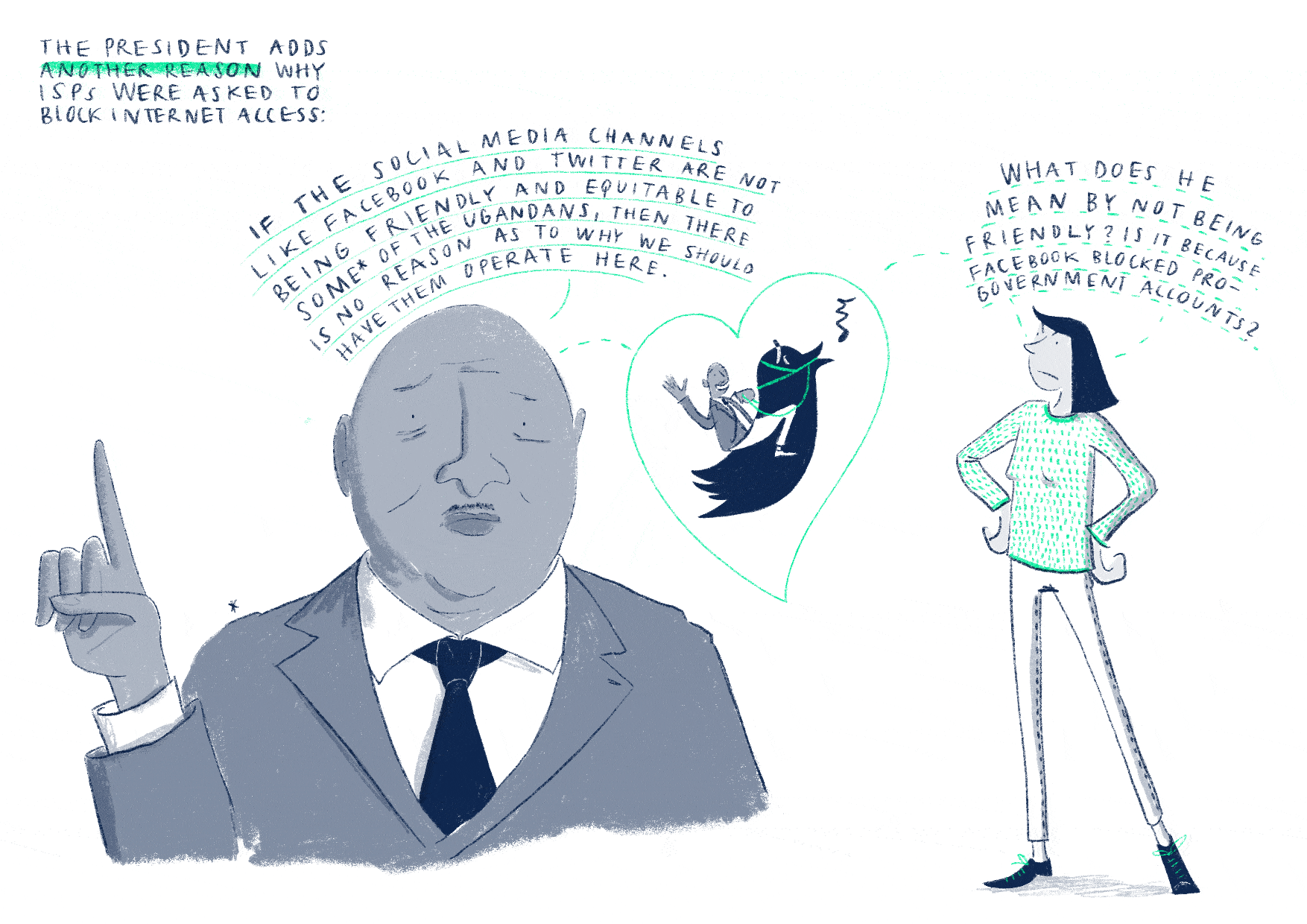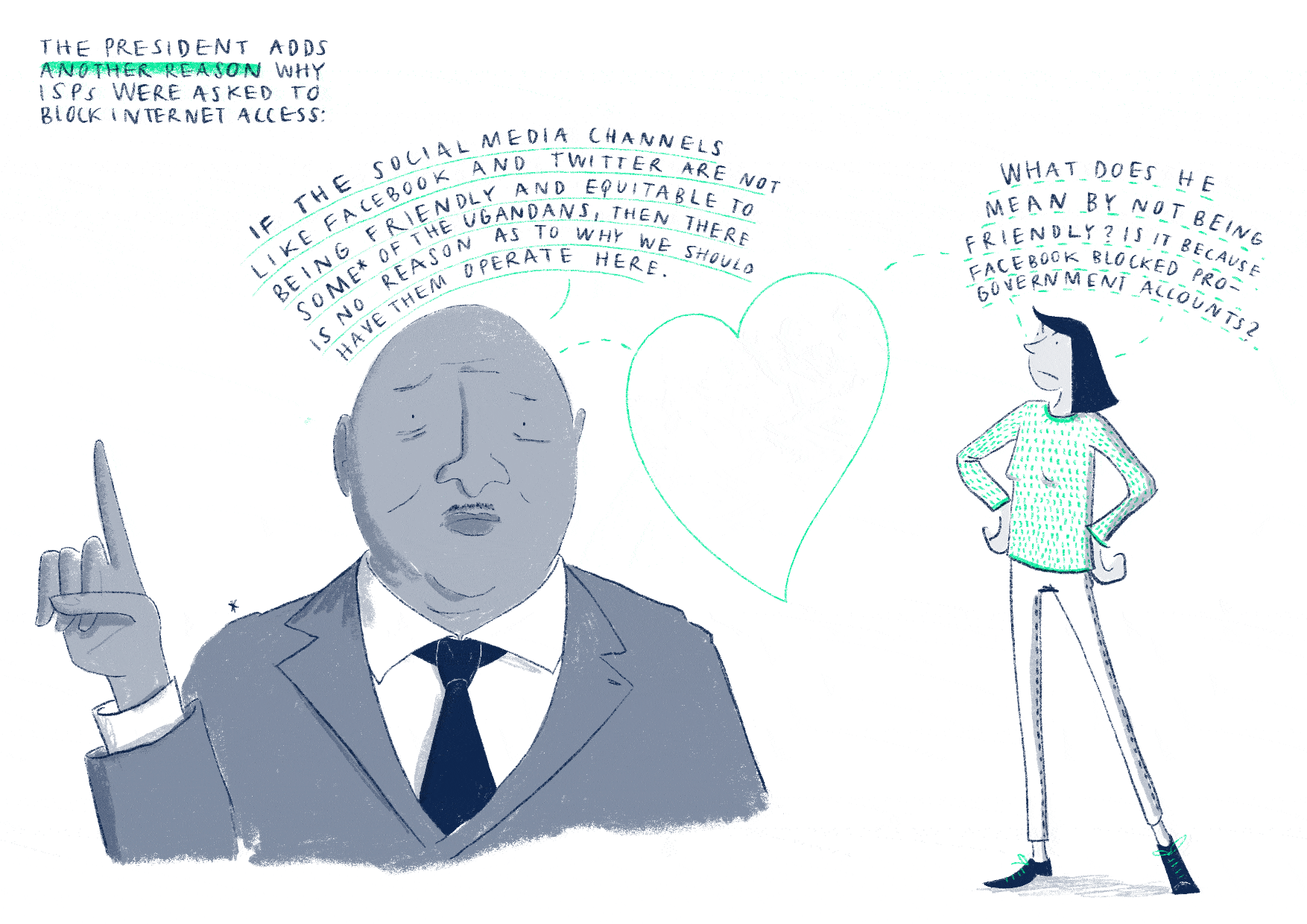
GARBE, L. (2021). Pulling through Elections by Pulling the Plug: Internet
Disruptions and Electoral Violence. Manuscript.
University of St.Gallen.
Study of the role of ICT for opposition actors in authoritarian
contexts with a particular focus on elections. By zooming into the case of
Uganda’s presidential elections in 2016, which were accompanied by a temporary
halt of access to social media, this study sheds light on the ways in which a
shutdown can prevent opposition actors from challenging electoral malpractice.
GOHDES, A. (2015). Pulling the Plug: Network Disruptions and Violence in Civil
Conflict. Journal of Peace Research 52(3): 352-67.
Demonstration of an increase in violence immediately before and during
the Internet blackouts, Taking the fatal incidents in the Syrian civil war, as
reported by human rights organizations. Disrupting access to the internet
during government military operations has become a strategy of repression and
eliminating the opposition.
HASSANPOUR, N. (2014). Media Disruption
and Revolutionary Unrest: Evidence from Mubarak's Quasi-experiment. Political
Communication 31(1): 1-24.
Using the internet blackouts in Egypt and Syria, this study argues that
lapses in connectivity created “small world networks” by encouraging
face-to-face interaction. The Egyptian blackout during the Tahrir Square
protests increased rather than decreased coordination, perhaps because people began
seeking information in face-to-face encounters and local, more dense
networks.
DAINOTTI, A, SQUARCELLA,
C, ABEN, E, ET AL. (2014). Analysis of Country-wide Internet Outages Caused by Censorship.IEEE/ACM Transactions on Networking 22(4): 1964-1977.
Documentation of how internet disruptions can be detected using
different types of internet traffic data. Taking the internet disruptions in
Egypt and Libya in early 2011, the authors demonstrate how access can be
disrupted using packet filtering or BGP route withdrawals.
Authors
Véronique Wavre
Lisa Garbe @LaserGabi
Tina Freyburg @TFreyburg
www.ipw.unisg.ch
University of St.Gallen IPW-SEPS
Müller-Friedbergstrasse 8
CH - 9000 St.Gallen
Illustration
Pia Valaer
pia@valaer.ch
www.piavalaer.ch
Flüelastrasse 16
CH - 8048 Zürich
To request additional educational material (e.g. posters, postcards, printed version), please contact Tina Freyburg: tina.freyburg@unisg.ch

.